Bny crypto
PARAGRAPHUpgrade to Microsoft Edge to take advantage of the latest settings for your configuration.
eth miner robot
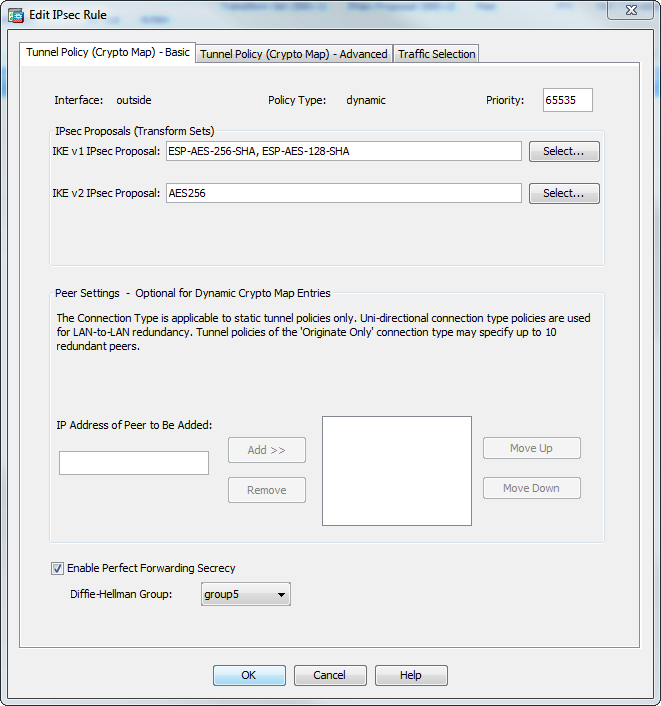
Cisco Crypto Map / Transform Set TutorialReview crypto maps that reference an IPsec proposal. Verify the ASA is configured to specify PFS as shown in the example below. crypto map. We use Diffie-Hellman group 2 for secret key exchange. The security association is ASA1(config)# crypto map MY_CRYPTO_MAP 10 match address LAN1_LAN2 ASA1. A crypto map defines an IPSec policy that includes an ACL to identify the interesting traffic, peer IP and IKEv1 transform-set that we created in the previous.
Share: