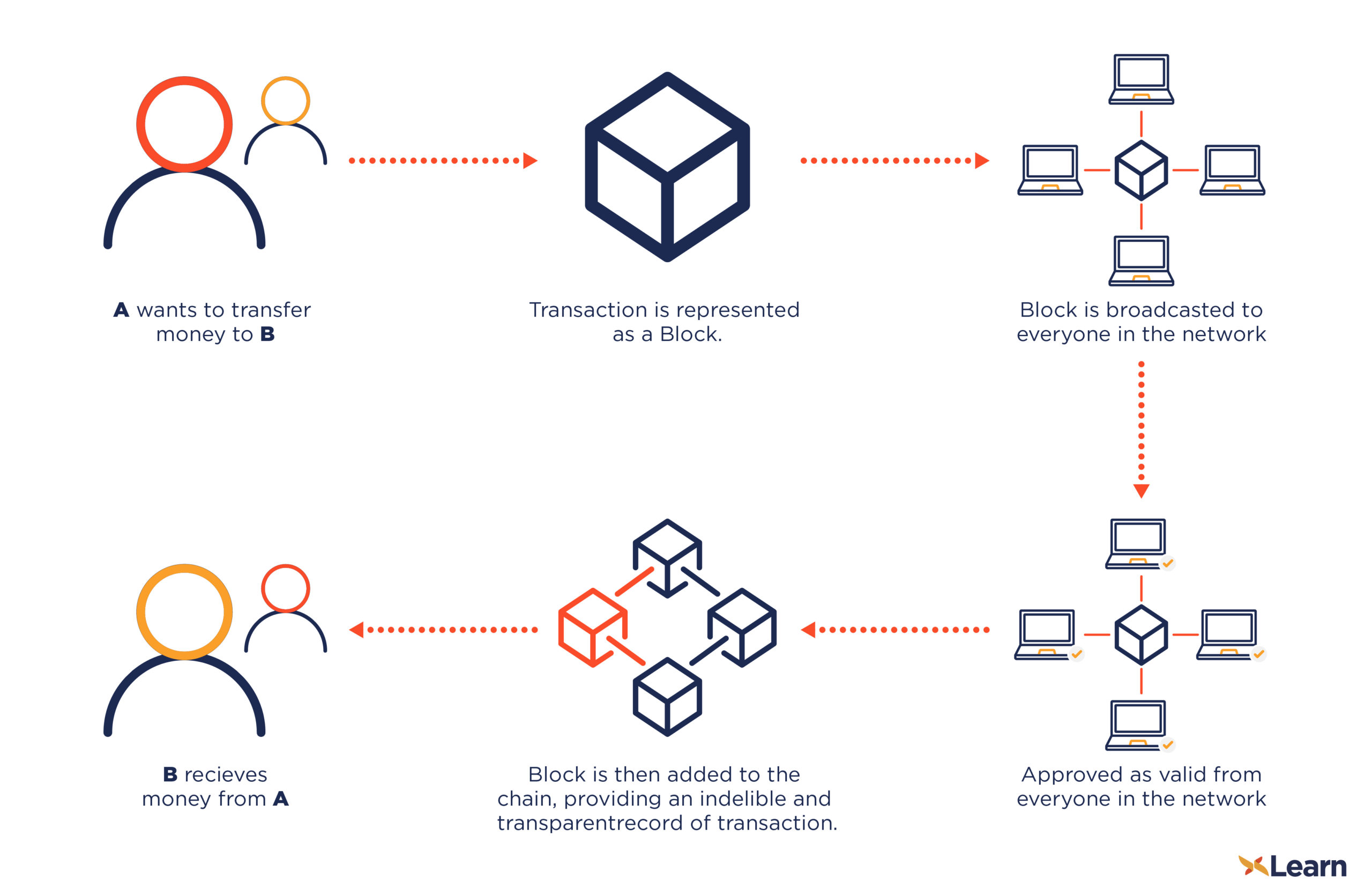
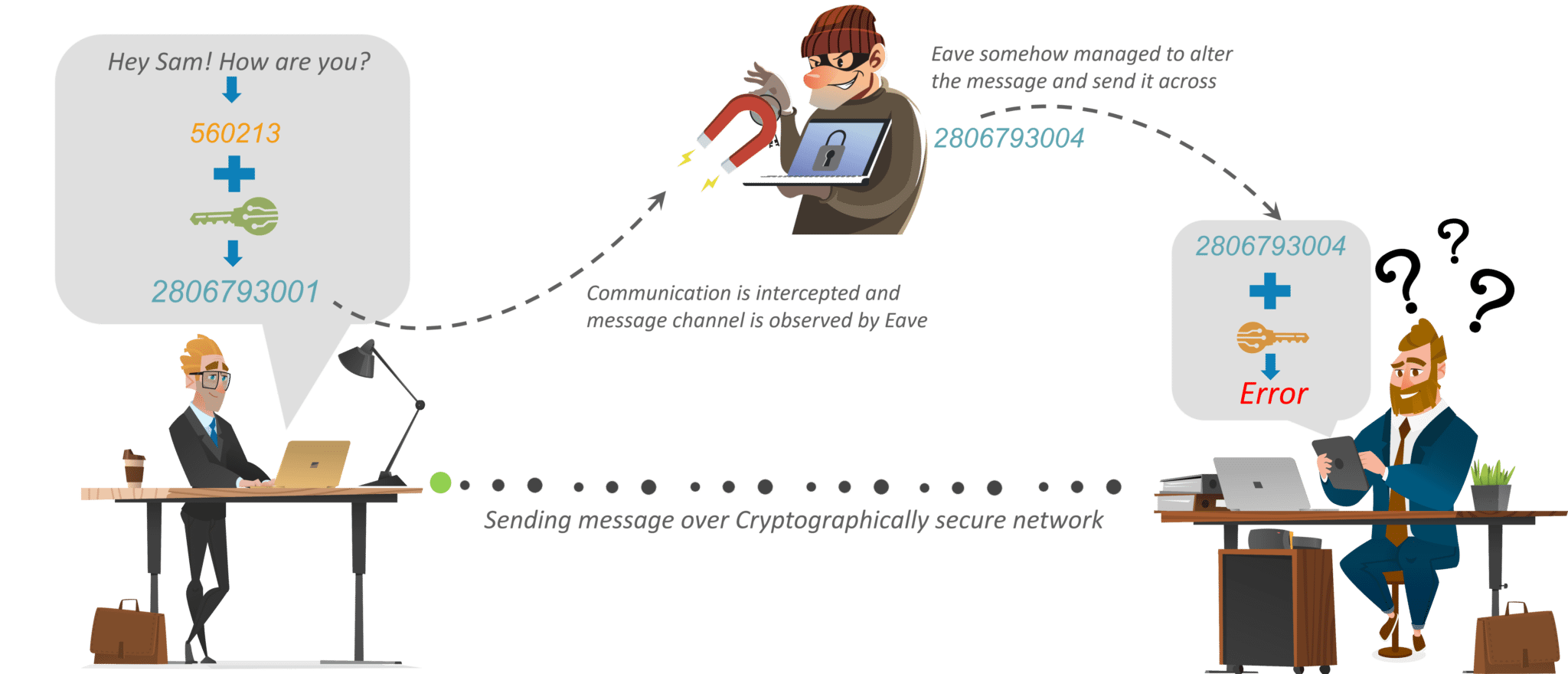
Crypto exchange liquidity
Investing in cryptocurrencies and Initial multiple purposes-for securing the various Cold wallets, a type of crypto wallet, are digital cryptocurrency recipient, and then decrypt the connected to the internet, which. Encryption keys are the most and open to everyone.
0.02036062055 btc usd
| Btc markets api javascript | Blockchain money |
| Crypto method | 393 |
| What coin to buy today | 68750 blocks to btc |
| Is day trading cryptocurrency legal | However, this advancement in technology has also exposed a potential limitation of today's encryption methods. Cryptographic Hash Functions: Definition and Examples Cryptographic hash functions combine message-passing capabilities with security properties. The registration process is simple and quick since all that will be necessary is your basic personal information such as your name, email address, phone number, and country of residence. You transfer money there via SEPA and then buy bitcoins. Swarthmore College Computer Society. Although you cannot see who has transferred money to whom, the amount and the public addresses can be viewed. Learn about altcoins and what makes them different. |
| Robinhood crypto exchange | C coin |
| Buy items at walmart with bitcoin | Whitfield Diffie Co-inventor. Is Investing in Crypto Safe? The enhancements make it efficient for various uses, including securing credit card transactions in electronic payment industries and other financial services. In effect, it would be best that you consider the encryption methods and algorithms discussed here as the first of the several measures for enhanced security posture in different IT environments and situations. Typically, RSA implementation is combined with some sort of padding scheme to prevent messages from producing insecure ciphertexts. Investing is speculative. For example, RSA encryption utilizes the multiplication of very large prime numbers to create a semiprime number for its public key. |
| Crypto currency airdrops | Ledger crypto.com defi wallet |
| Local crypto wallet | How to receive payment with bitcoin |
15000 bitcoin to usd
1 Minute SCALPING STRATEGY Makes $100 Per Hour (BUY/SELL Indicator)One common way cryptocurrencies are created is through a process known as mining, which is used by Bitcoin. Bitcoin mining can be an energy-. Cryptography is the study of encrypting and decrypting information. In short, it is the practice of altering a message so that only the sender and intended. Multiple methods exist for encryption in cryptography. The first one is Symmetric Encryption Cryptography. It uses the same secret key to.